Linux tcpdump Command Tutorial for Beginners (8 Examples)
Everytime you open a webpage on your computer, data packets are sent and received on your network interface. Sometimes, analyzing these packets becomes important for many reasons. Thankfully, Linux offers a command line utility that dumps information related to these data packets in output.
In this article, we will discuss the basics of the tool in question – tcpdump. But before we do that, it’s worth mentioning that all examples here have been tested on an Ubuntu 18.04 LTS machine.
Linux tcpdump command
The tcpdump command in Linux lets you dump traffic on a network. Following is its syntax in short:
tcpdump [OPTIONS]
Here’s the detailed syntax:
tcpdump [ -AbdDefhHIJKlLnNOpqStuUvxX# ] [ -B buffer_size ] [ -c count ] [ -C file_size ] [ -G rotate_seconds ] [ -F file ] [ -i interface ] [ -j tstamp_type ] [ -m module ] [ -M secret ] [ –number ] [ -Q in|out|inout ] [ -r file ] [ -V file ] [ -s snaplen ] [ -T type ] [ -w file ] [ -W filecount ] [ -E [email protected] algo:secret,… ] [ -y datalinktype ] [ -z postrotate-command ] [ -Z user ] [ –time-stamp-precision=tstamp_precision ] [ –immediate-mode ] [ –version ] [ expression ]
And here’s how the tool’s man page explains it:
Tcpdump prints out a description of the contents of packets on a network interface that match the
boolean expression; the description is preceded by a time stamp, printed, by default, as hours,
minutes, seconds, and fractions of a second since midnight.It can also be run with the -w flag, which causes it to save the packet data to a file for
later analysis, and/or with the -r flag, which causes it to read from a saved packet file rather
than to read packets from a network interface. It can also be run with the -V flag, which causes
it to read a list of saved packet files.In all cases, only packets that match expression will be processed by tcpdump.
Following are some Q&A styled examples that should give you a better idea on how the tcpdump command works.
Q1. How to use tcpdump?
Before using tcpdump to sniff data packets, you should ideally know which network interface you want the tool to work on. For a list of network interfaces available on the system, use the -D command line option with tcpdump.
tcpdump -D
Here’s how the man page explains this option:
Print the list of the network interfaces available on the system and on which tcpdump can capture
packets. For each network interface, a number and an interface name, possibly followed by a text
description of the interface, is printed. The interface name or the number can be supplied to the
-i flag to specify an interface on which to capture.This can be useful on systems that don't have a command to list them (e.g., Windows systems, or
UNIX systems lacking ifconfig -a); the number can be useful on Windows 2000 and later systems,
where the interface name is a somewhat complex string.The -D flag will not be supported if tcpdump was built with an older version of libpcap that
lacks the pcap_findalldevs() function.
For example, in my case, the following output was produced:
1.wlx18a6f713679b [Up, Running]
2.any (Pseudo-device that captures on all interfaces) [Up, Running]
3.lo [Up, Running, Loopback]
4.enp3s0 [Up]
5.nflog (Linux netfilter log (NFLOG) interface)
6.nfqueue (Linux netfilter queue (NFQUEUE) interface)
7.usbmon1 (USB bus number 1)
8.usbmon2 (USB bus number 2)
9.usbmon3 (USB bus number 3)
10.usbmon4 (USB bus number 4)
Now that you have a list of interfaces, you can choose one, and pass its name as input to the -i command line option of tcpdump. For example:
tcpdump -i wlx18a6f713679b
Following is a part of output produced by this command in my case:
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on wlx18a6f713679b, link-type EN10MB (Ethernet), capture size 262144 bytes
11:53:11.408964 IP 192.168.2.132.52898 > 239.255.255.250.3702: UDP, length 656
11:53:11.409492 IP himanshu.57383 > one.one.one.one.domain: 8572+ [1au] PTR? 250.255.255.239.in-addr.arpa. (57)
11:53:11.409588 IP 192.168.2.140.49690 > 239.255.255.250.1900: UDP, length 174
11:53:11.409954 IP 192.168.2.147.mdns > 224.0.0.251.mdns: 1 [2q] PTR (QU)? _%9E5E7C8F47989526C9BCD95D24084F6F0B27C5ED._sub._googlecast._tcp.local. PTR (QU)? _googlecast._tcp.local. (94)
11:53:11.499220 IP one.one.one.one.domain > himanshu.57383: 8572 NXDomain 0/1/1 (114)
11:53:11.499950 IP himanshu.34201 > one.one.one.one.domain: 12068+ [1au] PTR? 132.2.168.192.in-addr.arpa. (55)
11:53:11.591291 IP one.one.one.one.domain > himanshu.34201: 12068 NXDomain* 0/1/2 (278)
11:53:11.592195 IP himanshu.55501 > one.one.one.one.domain: 31630+ [1au] PTR? 1.1.1.1.in-addr.arpa. (49)
11:53:11.842603 IP himanshu.57253 > one.one.one.one.domain: 16905+ [1au] PTR? 140.2.168.192.in-addr.arpa. (55)
11:53:11.951226 IP himanshu.52662 > one.one.one.one.domain: 52377+ [1au] PTR? 251.0.0.224.in-addr.arpa. (53)
11:53:12.428931 IP 192.168.2.140.49690 > 239.255.255.250.1900: UDP, length 174
11:53:12.437905 IP 192.168.2.147.mdns > 224.0.0.251.mdns: 2 [2q] PTR (QM)? _%9E5E7C8F47989526C9BCD95D24084F6F0B27C5ED._sub._googlecast._tcp.local. PTR (QM)? _googlecast._tcp.local. (94)
11:53:12.438730 IP6 fe80::eccc:59f2:fc78:9e07.52899 > ff02::c.3702: UDP, length 656
11:53:12.439017 IP himanshu.33194 > one.one.one.one.domain: 15679+ [1au] PTR? c.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.2.0.f.f.ip6.arpa. (101)
11:53:12.572386 IP one.one.one.one.domain > himanshu.33194: 15679 NXDomain 0/1/1 (165)
11:53:12.642129 IP 192.168.2.11.mdns > 224.0.0.251.mdns: 0*- [0q] 1/0/3 PTR Google-Home-Mini-e3a3ae72a03e3d1c60d24653d4666ca6._googlecast._tcp.local. (356)
...
...
Q2. How to make tcpdump exit after receiving set number of packets?
This can be achieved using the -c command line option. For example, if you want tcpdump to only display information related to 10 packets, then you can do that in the following way:
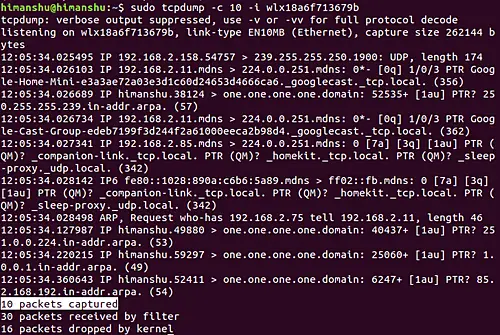
tcpdump -c 10
For example, in my case, I executed the following command:
tcpdump -c 10 -i wlx18a6f713679b
Following is the output that was produced:
So you can see 10 packets were captured.
Q3. How to make tcpdump display link-level header in output?
This can be done using the -e command line option. For example:
tcpdump -e -i wlx18a6f713679b
And here’s the output produced:
listening on wlx18a6f713679b, link-type EN10MB (Ethernet), capture size 262144 bytes
12:14:07.951396 3c:a8:2a:a7:7b:c1 (oui Unknown) > Broadcast, ethertype IPv4 (0x0800), length 197: 192.168.2.55.17500 > 255.255.255.255.17500: UDP, length 155
12:14:07.952111 3c:a8:2a:a7:7b:c1 (oui Unknown) > Broadcast, ethertype IPv4 (0x0800), length 197: 192.168.2.55.17500 > 192.168.2.255.17500: UDP, length 155
...
...
So you can see that link level headers were produced in the output.
Q4. How to make tcpdump display foreign IP addresses numerically?
This can be achieved using the -f command line option.
tcpdump -f -i [INTERFACE]
Making tcpdump display `foreign’ IPv4 addresses numerically rather than symbolically has its advantages in certain situations. One such example is mentioned in the tool’s man page:
this option is intended to get around serious brain damage in Sun's NIS server — usually it hangs
forever translating non-local internet numbers
Q5. How to make tcpdump produce packet numbers in output?
To make tcpdump produce packet numbers in output, use the –number command line option.
For example, I executed the following command:
tcpdump –number -i wlx18a6f713679b
And here’s part of the output that was produced:
listening on wlx18a6f713679b, link-type EN10MB (Ethernet), capture size 262144 bytes
1 12:38:35.522944 ARP, Request who-has 192.168.2.196 tell _gateway, length 46
2 12:38:35.523265 IP6 fe80::8ab4:a6ff:fe9d:a6bb > ff02::16: HBH ICMP6, multicast listener report v2, 1 group record(s), length 28
3 12:38:35.523578 IP6 fe80::8ab4:a6ff:fe9d:a6bb > ip6-allrouters: ICMP6, router solicitation, length 16
4 12:38:35.523861 ARP, Request who-has 192.168.2.15 tell 192.168.2.170, length 28
...
...
...
So you can see each line now begins with a number.
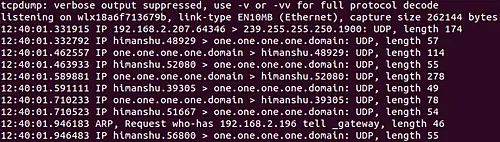
Q6. How to make tcpdump print shorter output?
This can be done using the -q command line option. Here’s how the tool’s man page explains it:
Quick (quiet?) output. Print less protocol information so output lines are shorter.
Following is an example of this option:
So you can see less information was produced in output this time.
Q7. How to omit timestamp info from tcpdump output?
Use the -t command line option for this. Here’s an example command:
tcpdump -t -i wlx18a6f713679b
And following is its output:
listening on wlx18a6f713679b, link-type EN10MB (Ethernet), capture size 262144 bytes
IP himanshu.56992 > mails11.telegram.org.https: Flags [.], ack 3090054317, win 965, options [nop,nop,TS val 226976758 ecr 3781653930], length 0
IP himanshu.41122 > one.one.one.one.domain: 12755+ [1au] PTR? 22.171.154.149.in-addr.arpa. (56)
IP mails11.telegram.org.https > himanshu.56824: Flags [.], ack 273652159, win 1001, options [nop,nop,TS val 3781656472 ecr 226966324], length 0
ARP, Request who-has 192.168.2.48 tell _gateway, length 46
ARP, Request who-has 192.168.2.135 tell _gateway, length 46
...
...
So you can see timestamp information (which is generally in the beginning of each line) isn’t present in output now.
Q8. How to make tcpdump produce detailed output?
You can use the -v command line option in this case. Following is how the tool’s man page explains this option:
tcpdump -v -i [INTERFACE]
When parsing and printing, produce (slightly more) verbose output. For example, the time to live,
identification, total length and options in an IP packet are printed. Also enables additional
packet integrity checks such as verifying the IP and ICMP header checksum.When writing to a file with the -w option, report, every 10 seconds, the number of packets captured
Conclusion
We’ve just scratched the surface here as the tcpdump command offers a lot of command line options. Once you are done practicing these, you can head to the tool’s man page to learn more about it.